COOPERATION MODEL
ARTIFICIAL INTELLIGENCE
PRODUCT ENGINEERING
DevOps & Cloud
LOW-CODE/NO-CODE DEVELOPMENT
INDUSTRY
FRONTEND DEVELOPMENT
CLOUD DEVELOPMENT
MOBILE APP DEVELOPMENT
LOW CODE/ NO CODE DEVELOPMENT
EMERGING TECHNOLOGIES








Java is a renowned programming language for building enterprise applications, web applications, and cloud applications. Among the numerous benefits of Java, security is also a key one. Among the best programming languages for security, Java stands out as one of the top choices. But even though Java comes with strong built-in security features, developers still need to follow the right practices to avoid common vulnerabilities.
Today, we will discuss Java security best practices that you can follow to secure your application. Writing secure Java code is essential to protect your users and your application. We'll cover practices and also learn how to secure Java code, which tools can help, and why Java application security testing is important.
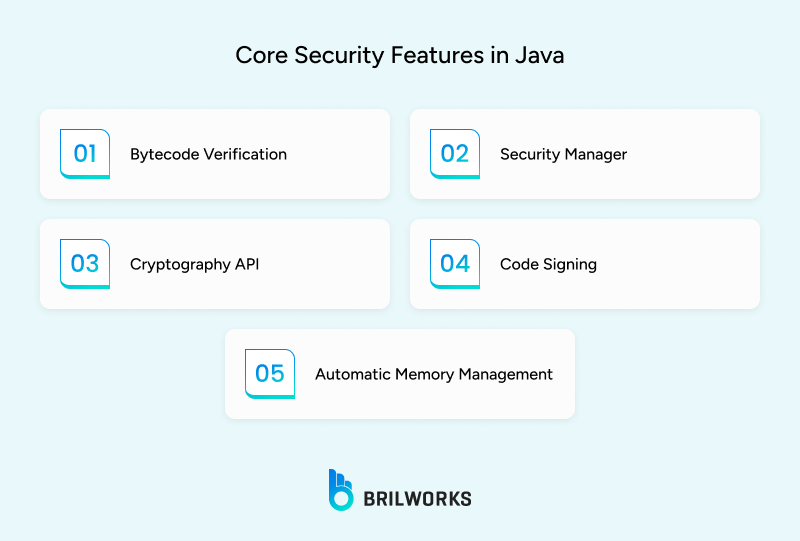
Java has long been considered a leading choice for building secure applications, particularly in environments where access control is critical. Several intrinsic features and architectural decisions in Java directly address security concerns.
Bytecode Verification: Every time a Java class is loaded, the JVM checks its bytecode to make sure it follows strict rules. This helps block code that tries to do unsafe operations.
Automatic Memory Management: Java's garbage collection helps reduce memory-related issues like buffer overflows, which are common in other languages.
Security Manager: Java allows developers to run code in restricted environment. This means untrusted code (like plugins or scripts) can be controlled and limited in what it can access.
Cryptography API: Java has built-in support for encryption, decryption, hashing, and secure communication. These tools make it easier to protect sensitive data.
Code Signing: Java supports digital signatures and permission-based access, so you can control what different parts of your application are allowed to do.
Thanks to these features, many organizations trust Java to power secure systems. But these features are only effective when used properly. That's why following best practices for Java security is important.
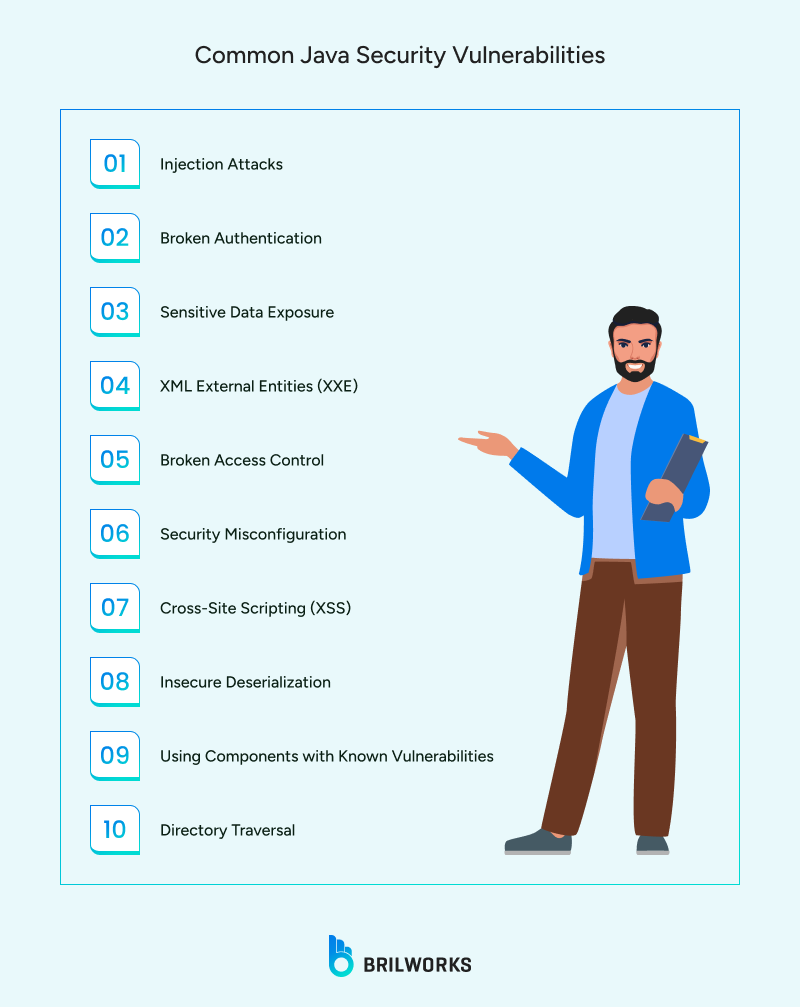
Java offers many built-in security features that can help you fortify your application. However, vulnerabilities can still occur, often due to small oversights in the code. Understanding these issues is an important first step in writing secure Java code. Here’s a breakdown of the most common risks developers need to watch for:
Attackers can insert malicious commands into SQL queries when user input is added directly without validation. For instance, 'OR '1'+'1 could get past login security measures and expose private information. Using prepared statements with parameterized queries rather than dynamic SQL is the answer.
LDAP injection, command injection, XPath injection, and NoSQL injection are examples of similar attacks. They all occur when commands or queries are constructed using unsafe input, which may result in remote code execution or unauthorized access.
Attackers can take over accounts through weak authentication techniques like hardcoded credentials, no rate limiting, or plaintext password storage. For example, a servlet is susceptible to brute-force or session-fixation attacks if it fails to securely store passwords or secure session tokens.
Sensitive information can be leaked by Java apps that improperly handle data encryption. Serious breaches can result from using antiquated algorithms (like DES), not encrypting data while it's in transit or at rest, or improperly handling encryption keys.
Attackers can fool a Java application into reading local files or sending network requests to malicious servers if it parses XML without turning off external entities. Data exposure or even denial of service may arise from this.
Attackers can obtain unauthorized data or carry out restricted actions if your application only uses client-side logic or fails to verify user roles on the server. In any secure system, access rights must be properly validated.
Default settings, exposed error messages, missing headers, or debug endpoints can all open the door for attackers. Even leaving sample files or admin consoles accessible can create unnecessary risk.
When Java web apps display user input without escaping it, attackers can inject scripts into web pages. These scripts can hijack sessions, steal data, or deface the application. Always sanitize and encode user input in the UI layer.
Java supports object serialization, but if untrusted data is deserialized, it can lead to remote code execution (RCE). This vulnerability has been exploited in real-world attacks, often affecting major Java frameworks and apps.
Many Java security incidents stem from outdated libraries. The Log4j vulnerability (Log4Shell) showed how one popular tool can expose thousands of systems. Always monitor dependencies and apply updates promptly.
If file paths aren't validated properly, attackers can manipulate them to access files outside the intended folder. For example, using ../../ in a path could allow someone to read sensitive configuration files from the server.
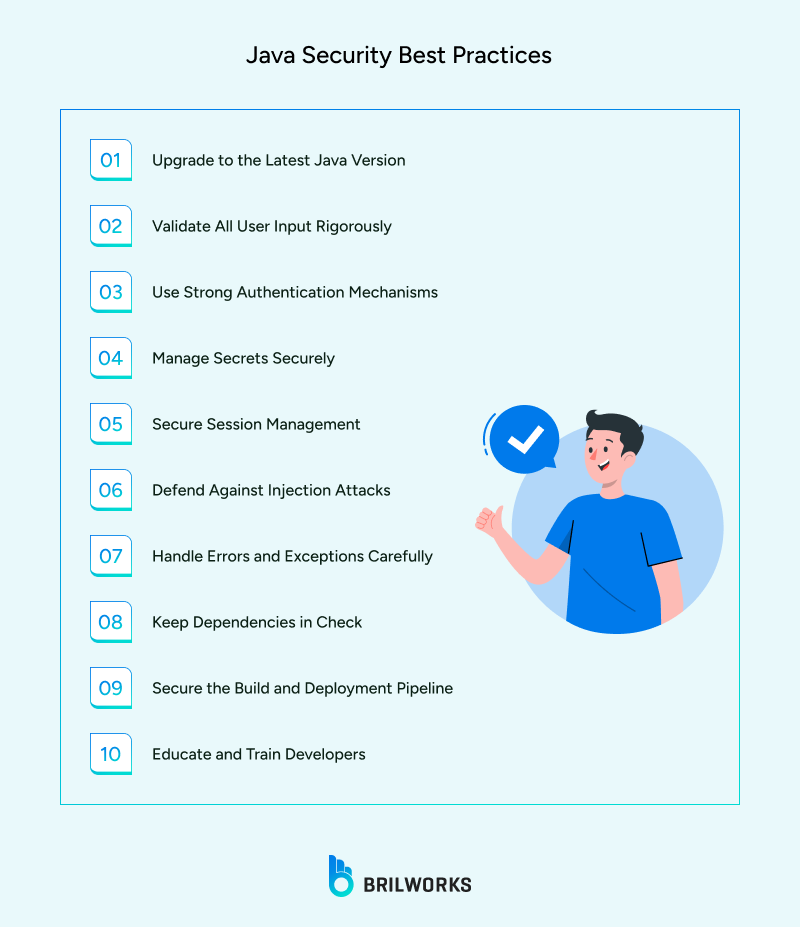
Common security threats we discussed are not inevitable. Most can be sidestepped entirely if you stick to a few solid Java security practices from the start. Not only does that save you trouble early on, it also sets your app up to be more secure over time. So if you are scratching your head about how to secure Java code, these practices are a smart way to start heading in the right direction.
One of the easiest ways to keep your Java apps safe is to keep your Java updated. Each new Java version release has security patches updated, which seal up the cracks found in older versions. Sticking with an outdated build can leave the door open to bugs and exploits that hackers already know how to find. Make a habit of updating your Java to the latest version. It's a small effort that can make a big difference.
User input is one of the easiest ways for things to go wrong in an application. Someone types something into a form or sends data through an API, and suddenly you are dealing with more than you bargained for. In Java, this is where input validation becomes essential. Make sure the data looks the way it should. Clean up anything suspicious. Stick to approved formats and known good values instead of trying to block bad ones. These small checks can stop a lot of serious attacks before they even start.
If your authentication is weak, it is only a matter of time before someone walks right in. Hardcoded usernames, simple password checks, and shortcuts like that leave your system wide open. A better approach is to use strong password hashing with something like bcrypt or PBKDF2. Add another layer by requiring multi-factor authentication, which makes a huge difference. You do not have to build it all yourself either. Tools like Spring Security take care of the heavy lifting so you can focus on building securely from the start.
Burying sensitive info inside your code might seem convenient, but it is a mistake. Things like API keys, database credentials, or encryption secrets do not belong in your source files. A smarter route is to move them into environment variables or store them using tools built for the job, like AWS Secrets Manager or HashiCorp Vault. This makes it much easier to manage who gets access and helps prevent those “oops” moments that lead to leaks.
Session tokens are like keys that keep users logged in. But if those keys are easy to guess, last forever, or get passed around carelessly, trouble follows. Use tokens that are truly random and make sure they expire after a reasonable amount of time. When storing them in cookies, turn on the HttpOnly and Secure flags to keep them out of reach. And do not forget to generate a fresh token after someone logs in or out. That simple step can shut down a whole class of session-based attacks before they even begin.
Injection attacks show up when you let outside data sneak into places it does not belong. That includes database queries, LDAP lookups, or even system commands. Writing raw SQL with user input stitched right into the string is like handing the attacker a pen and letting them finish your code. Java gives you a safer option. Use PreparedStatement to keep your logic and user input in separate lanes. It is a small shift, but it stops a whole category of attacks before they can do any damage.
Detailed error messages might be great when you're debugging, but in production, they can spill more than you'd like. Attackers pay close attention to what your app gives away when something breaks. A stack trace might tell them exactly where to poke next. The better move is to log the full error behind the scenes and show users something simple and vague. Java logging tools like Logback or Log4j can help you do this well—just make sure you're using them safely and not writing sensitive info to your logs by accident.
Pulling in third-party libraries is common in Java projects, and for good reason—it saves time and effort. But every outside dependency brings its own baggage. If one of those libraries has a known vulnerability, your application inherits that risk. That is why it is smart to scan your dependencies often using tools like Snyk or OWASP Dependency-Check. They can flag issues before they turn into real problems. And if a library has not seen updates in years, it is probably time to let it go, even if it still seems to work fine.
It is easy to focus on writing secure code and forget that the build pipeline needs just as much protection. If someone slips into your CI or CD system, they do not need to hack your app—they can quietly plant their own code and wait. Lock down access to your pipeline with strong permissions. Only trusted people should be able to push changes to key branches. Sign your build artifacts so you know they came from you, and not someone else. Think of your deployment systems like you would a production server—because once they are compromised, everything that follows is too.
You can have all the tools, scanners, and policies in place, but at the end of the day, it is people who write the code. That is where most security mistakes begin—and where they can be caught early too. Developers need more than rules. They need to know what to look out for. A short workshop, a peer review, even a quick run-through of the OWASP Top 10 now and then can go a long way. When your team starts thinking about security as they code, not after, you are already ahead of most.
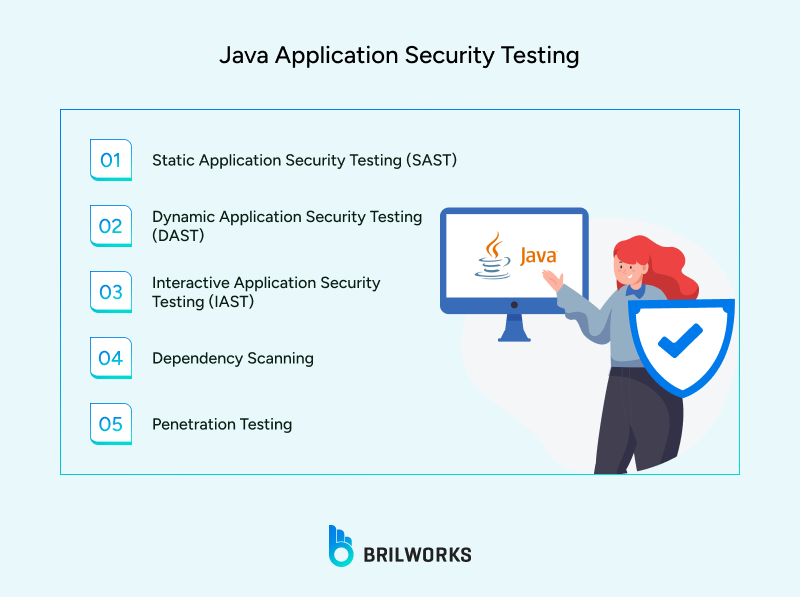
You can follow every best practice and still miss something. That is just how software works. Even solid, well-written Java code can hide vulnerabilities you did not see coming. That is why security testing matters. It gives you a chance to spot issues before someone else does. The key is to make testing a regular part of your process, not an afterthought.
Static analysis is like giving your code a security review before it ever runs. It looks through your Java source files and flags things that might go wrong—like hardcoded passwords, weak encryption choices, or sloppy input handling. Tools like FindSecBugs or SonarQube can catch these issues early, when fixing them is still simple. The goal is not just to spot bugs, but to build good security habits into your code from day one.
Dynamic testing takes a different approach. Instead of reading your code, it interacts with the app while it is live. It looks for things like broken authentication, sloppy session handling, or leaks of sensitive information. What makes it powerful is that it catches issues that only appear when the app is actually running, the kind of stuff you would miss just by reading code.
Interactive testing blends the strengths of both static and dynamic analysis. It watches your app in real time as it runs, paying attention to both the code and what actually happens during execution. If something looks off—like a risky call or unexpected behavior—it flags it right away. Because it sees both the structure and the flow, IAST can catch problems that SAST and DAST might overlook on their own.
Chances are your Java project leans on a handful of third-party libraries. But not all libraries are safe to use. Some carry known vulnerabilities that can quietly put your entire app at risk. That is where tools like Snyk, OWASP Dependency-Check, or GitHub’s security alerts come in handy. They scan your dependencies and warn you about any trouble. Staying on top of this stuff is a key part of writing Java code that holds up under pressure.
This is where real people step in—ethical hackers who try to break into your app just like an attacker would. Unlike automated scans, this is hands-on work. They look for cracks in your defenses that tools might overlook. If your app deals with sensitive information or is exposed to the public, regular penetration testing can uncover hidden risks before someone else finds them the hard way.
Use this checklist as a quick reference while developing, reviewing, or maintaining your Java applications:
Are you using the latest stable version of Java?
Is input validation in place for all user inputs?
Are sensitive data fields (e.g., passwords, tokens) encrypted properly?
Are you avoiding hardcoded secrets or credentials?
Are error messages free from stack traces or internal logic exposure?
Is password storage using strong hashing (like bcrypt)?
Is multi-factor authentication implemented where needed?
Are sessions expiring after inactivity?
Are secure and HttpOnly flags set for cookies?
Are user roles and permissions strictly enforced server-side?
Is business logic protected from unauthorized access or misuse?
Have you scanned dependencies for known vulnerabilities?
Are unused libraries and features removed?
Are security tests (e.g., static analysis, penetration tests) part of your CI/CD pipeline?
Are security headers configured properly?
Is HTTPS enforced across the application?
Are default passwords, ports, and debug endpoints disabled or secured?
Are developers aware of Java security best practices?
Has your team been trained on common Java vulnerabilities like XSS, XXE, and insecure deserialization?
Are you regularly reviewing and updating your secure coding standards?
Java has a vast ecosystem of frameworks, IDEs, tools, and APIs. You can make use of these technologies to make your next Java application even more secure. Java is not a silver bullet, though; it has its limitations like other programming languages. But with the right approach, it is a reliable tech stack for your business. That is why many companies like Google, Netflix, or Amazon use Java for their backend development.
Moreover, security is not the final step of the development process. It’s something that needs to be built into every stage of your Java application. From understanding common vulnerabilities to applying proven Java security best practices, securing your code requires consistency, awareness, and the right tools.
If you are still unsure about your security, don't hesitate to seek our professional help. As a mobile app and software development company, we have worked on many such projects where security is a top priority. Let our vetted Java developers take over your project and help you fortify your Java application.
Key practices include input validation, keeping Java versions up to date, secure session management, using strong authentication, managing secrets properly, and regular Java application security testing.
To write secure Java code, avoid hardcoding sensitive data, use prepared statements to prevent injection attacks, validate user input, and follow secure coding standards from the start of development.
Java includes built-in security features like the Security Manager, bytecode verification, and automatic memory management, which make it a strong choice for building secure applications.
Tools like OWASP Dependency-Check, SpotBugs (with the Find Security Bugs plugin), and static analysis tools help identify vulnerabilities and ensure your code follows Java security best practices.
Java application security testing should be done regularly—during development, before deployment, and as part of routine maintenance—to catch issues early and reduce risk over time.
Get In Touch
Contact us for your software development requirements
Get In Touch
Contact us for your software development requirements