COOPERATION MODEL
ARTIFICIAL INTELLIGENCE
PRODUCT ENGINEERING
DevOps & Cloud
LOW-CODE/NO-CODE DEVELOPMENT
INDUSTRY
FRONTEND DEVELOPMENT
CLOUD DEVELOPMENT
MOBILE APP DEVELOPMENT
LOW CODE/ NO CODE DEVELOPMENT
EMERGING TECHNOLOGIES








Node.js is a runtime environment that enables developers to use JavaScript beyond web browsers (or the front end) using various frameworks. It runs on Chrome's V8 engine, allowing JavaScript developers to apply their skills to back-end development using the same language.
While Node.js is secure itself, it relies on open-source packages, as in the fast-paced world, companies and developers do not want to invest their time in reinventing the wheel. The packages make development easy and fast. However, this convenience can also introduce vulnerabilities in the application.
NPM, an open-source platform containing over two million packages, serves as a valuable resource by providing millions of packages to JavaScript developers. On the one hand, it makes it easy to use packages. On the other hand, it may pose potential risks.
Node.js developers heavily depend on open-source third-party packages.
In 2021, 77 percent of respondents from the United States report using open source to modernize their IT infrastructure, a report from Statista shows.
Despite the fact that over 78% of organizations utilize open-source projects, only about 40% of organizations employ formal security rating tools to assess the security of these packages. Furthermore, only about 27% of open-source projects are audited on a regular basis, according to a report.
Like others, NodeJS applications are vulnerable to security breaches. Therefore, it becomes imperative to take the necessary steps to enforce strong security measures.
This article is a compilation of expert tips and advice on securing Nodejs applications. However, if you need technical assistance to enforce strong security measures on your existing app, you can explore our Nodejs development services. Our team of professional IT experts will thoroughly assess your application for security vulnerabilities.
Strong authentication is all about implementing the latest security measures to safeguard sensitive pieces of information. As you know, data breaches are no longer a rarity. They are a daily occurrence, and even the biggest tech companies are not immune. In recent years, Google, Twitter, and other big-name companies have all experienced data breaches that led to them redefining their authentication mechanism. Here are a few methods to be considered:
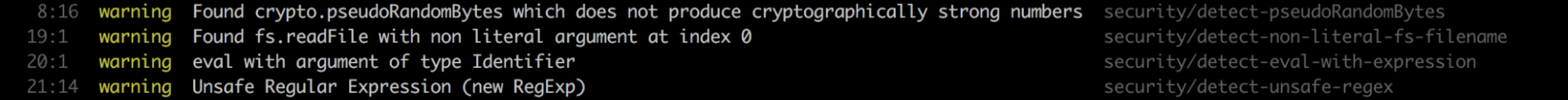
These tools help you identify security weaknesses such as unsafe RegEx, unsafe use of eval(), use of non-literal filenames, etc., in your node applications when you write code. Overall, they can help detect these security flaws easily.
Eslint and Tslint are well-known code analytics tools for JavaScript and TypeScript projects for security checks in Node applications.
An example:
Limiting concurrent requests helps prevent Nodejs applications from being unresponsive due to overwhelming requests at the same time. By using a middleware or balancer, you can limit the number of requests. Ngnix is a widely used service for load balancing; however, you can also make use of middleware express-rate-limiter or rate-limiter-flexible package.
Node.js includes an EventLoop to run JavaScript code and a Worker Pool for intensive tasks, which makes it a scalable platform that can handle too many requests. All incoming requests and outgoing responses flow through the Event Loop.
Node.js leverages V8 (JavaScript engine) for code execution, which is fairly fast for many common operations. However, if callbacks have large complexities or regexp and JSON operations occur in your program, it can lead to Event Loop blocking.
The common issues that may trigger Event Loop blocking are vulnerable regular expressions. Follow the tips below to avoid Event Loop blocking.
It doesn’t have any built-in logging tools, but you will find a wealth of third-party tools for logging and monitoring your code, which can significantly reduce manual labor. Some popular Nodejs logging frameworks are Winston, Pino, and Bunyan.
If you seek simpler and lighter logging modules, bole and loglevel are great to utilize.
Logging is essential for catching errors and staying informed about recent developments in your application, allowing you to gain insights into its real-world behavior and identify opportunities for performance optimization. It helps you in many ways, including identifying potential security threats.
While logging, keep note of the following points:
In the time when SSL/TLS certificates are free and easy to configure, you should not delve much more into the advantages and disadvantages of using a secure server because the security outweighs the minimal overhead of using HTTPS compared to HTTP.
Node.js is a popular JavaScript runtime environment used to build a wide range of applications, from simple websites to complex web services. However, Node.js applications can be vulnerable to a variety of attacks if they are not security checks are not properly performed.
This article outlines some essential Node.js security best practices that you should follow to craft secure code that protects your application. By following these best practices, you can help to protect your backend web applications from common attacks.
If you find that your Node.js application needs a security check, you can connect with us, and we will offer you custom Node.js development services to enhance your application's security and performance.
Get In Touch
Contact us for your software development requirements
Get In Touch
Contact us for your software development requirements