COOPERATION MODEL
ARTIFICIAL INTELLIGENCE
PRODUCT ENGINEERING
DevOps & Cloud
LOW-CODE/NO-CODE DEVELOPMENT
INDUSTRY
FRONTEND DEVELOPMENT
CLOUD DEVELOPMENT
MOBILE APP DEVELOPMENT
LOW CODE/ NO CODE DEVELOPMENT
EMERGING TECHNOLOGIES








Managing React Native environment variables is one of the most important practices for building apps that are secure, flexible, and easy to maintain. Using tools like react-native-config and process.env, you can separate sensitive information from your code, handle multiple environments such as development, staging, and production, and make sure your React Native app development workflow stays smooth and reliable.
Through our experience with React Native app development, we have seen how proper environment management can prevent mistakes, improve security, and save time. In this guide, we will cover why environment variables matter, how to set them up, best practices, and advanced techniques to make your project more maintainable.
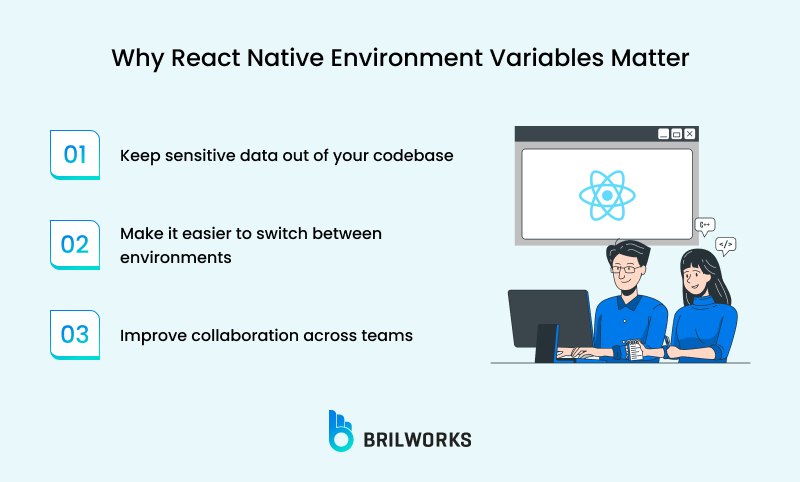
Even though environment variables might seem like a small piece of your project, they are crucial for building secure and maintainable React Native apps. Since React Native lets you share code between iOS and Android, managing environment variables properly ensures consistent behavior across platforms and keeps sensitive information safe.
Here’s why you should pay attention:
Hardcoding API keys, server URLs, or tokens in your code can create serious security risks. Environment variables let you store this data separately, making updates easier and reducing the chance of exposing secrets if your code is shared.
Your development, staging, and production environments often require different settings. Environment variables make it possible to switch without changing the code manually. Just define variables per environment, and your build process handles the rest.
When multiple developers work on a React Native app for an enterprise, sharing code is inevitable. Environment variables let each developer use their own configuration without exposing sensitive data, preventing accidental leaks and simplifying onboarding.
Choosing the right setup depends on whether you are working on a bare React Native project, using Expo, or dealing with native modules. Here’s a breakdown of the most common methods:

Libraries like react-native-config or react-native-dotenv (deprecated) allow you to define key-value pairs in .env files and load them during build time.
Pros
Easy to set up and maintain
Familiar .env syntax
Supports multiple environments (.env.development, .env.staging, .env.production)
Cons
Mishandled files can expose sensitive information
Some variables may require native linking for full functionality
You can create a custom file, such as config.js:
// config.js
export const API_URL = __DEV__
? 'https://dev.example.com'
: 'https://prod.example.com';Pros: No additional libraries, easy to customize
Cons: Values are bundled in your code, not suitable for sensitive data, and cannot change at runtime
iOS: Use Xcode build schemes or Info.plist settings
Android: Define build flavors and access variables via BuildConfig
Pros: Fine-grained control over platform behavior
Cons: Requires native development knowledge, harder to maintain than JavaScript-based approaches
Expo supports .env files, but public variables must be prefixed with
EXPO_PUBLIC_.
EXPO_PUBLIC_API_URL=https://staging.example.com
Access them in your code:
const apiUrl = process.env.EXPO_PUBLIC_API_URL;
Expo automatically loads .env, .env.local, or .env.production based on priority. Remember, never store sensitive information in EXPO_PUBLIC_ variables, since they are visible in your JavaScript bundle.
For many projects, react-native-config is the most reliable option. It separates configuration from your code without cluttering it.
npm install react-native-configLink it for older React Native versions:
npx react-native link react-native-configWorks with Expo bare workflow; for managed workflow, use Expo’s built-in support.
API_URL=https://api.staging.example.com
API_KEY=your-secret-api-keyimport Config from 'react-native-config';
const apiUrl = Config.API_URL;
console.log(apiUrl); // https://api.staging.example.com
Create .env.development, .env.staging, .env.production and update your build scripts:
Android: ENVFILE=.env.staging ./gradlew assembleRelease
iOS: Set ENVFILE in your build scheme
Sensitive data should not be stored directly in .env. Use secure storage or inject secrets via CI/CD pipelines when needed.
react-native-config: Load env files for JS and native code
Expo CLI: Built-in support for .env files
dotenv: Useful for loading .env files during development
Secrets Managers: AWS Secrets Manager, Azure Key Vault, HashiCorp Vault
VS Code + Extensions: DotENV, React Native Tools, Prettier, ESLint
Never commit .env files: Add .env* to .gitignore
Use separate files for each environment: .env.development, .env.staging, .env.production
Avoid exposing secrets in the frontend: Sensitive variables belong on the backend
Keep variable names clear and consistent: Use uppercase with underscores, e.g., API_URL, ENABLE_FEATURE_X
Document your environment setup – Internal documentation helps onboarding
Use .env.example: Provide placeholder values for teammates

Define a typed interface to get autocompletion and compile-time checks:
declare module 'react-native-config' {
interface EnvVars {
API_URL: string;
ENABLE_LOGGING: string;
}
const Config: EnvVars;
export default Config;
}Inject environment variables during deployment using GitHub Actions, GitLab CI, or CircleCI. This keeps secrets out of version control and ensures per-environment deployment.
Use environment variables to enable or disable features dynamically. This is useful for beta features, A/B testing, or staged rollouts.
Exposing sensitive data in the JS bundle: Use secure storage or inject secrets at runtime
Missing fallbacks: Always provide defaults, e.g., Config.API_URL || 'https://default.example.com'
Not rebuilding the app: Changes require a rebuild, not just hot reload
Committing .env files accidentally: Revoke secrets immediately if this happens
Typos or inconsistent naming: Standardize variable names and maintain a .env.example
Environment variables may not be the most exciting part of development, but they are essential for secure, flexible, and scalable React Native app development. By using .env files, react-native-config, and integrating with CI/CD pipelines, you keep your app maintainable and production-ready.
If you are building a React Native app and need expert help with configurations, optimizing environments, or scaling your application, our team delivers secure, high-performance React Native solutions tailored to your goals.
Use .env files with the EXPO_PUBLIC_ prefix and access them via process.env.
Only non-sensitive data should be stored. Use secure storage for private keys.
react-native-dotenv is deprecated. react-native-config offers better integration and multi-environment support.
Create separate .env files and use react-native-config or Expo’s workflow to access them.
Get In Touch
Contact us for your software development requirements
Get In Touch
Contact us for your software development requirements