COOPERATION MODEL
ARTIFICIAL INTELLIGENCE
PRODUCT ENGINEERING
DevOps & Cloud
LOW-CODE/NO-CODE DEVELOPMENT
INDUSTRY
FRONTEND DEVELOPMENT
CLOUD DEVELOPMENT
MOBILE APP DEVELOPMENT
LOW CODE/ NO CODE DEVELOPMENT
EMERGING TECHNOLOGIES








White label development simply allows companies to put their brand on a pre-made platform and call it their own, while saving time, money, and time to market. It's a quick way to get an app developed. However, security could be a big concern. Big clients are not only interested in knowing, "How secure is your app?"
We have received this kind of question countless times: "Can you guarantee that a client's custom branding doesn't allow hackers to insert malicious code?"
It's a very realistic concern that keeps CTOs up at night. Security review processes are not a "would be nice to have" step; they are critical for an app development company.
In this blog, we will outline the essential layers of security to help you develop a highly secure white-label product.
As you are aware, a white-label product accommodates multiple tenants within a single platform. We call it a shared architecture. Clients have control over branding. However, in this architecture, the tenant boundaries appear blurred. An injected client code fluctuation can pose a risk to compliance obligations. How does a business create a security strategy at scale?
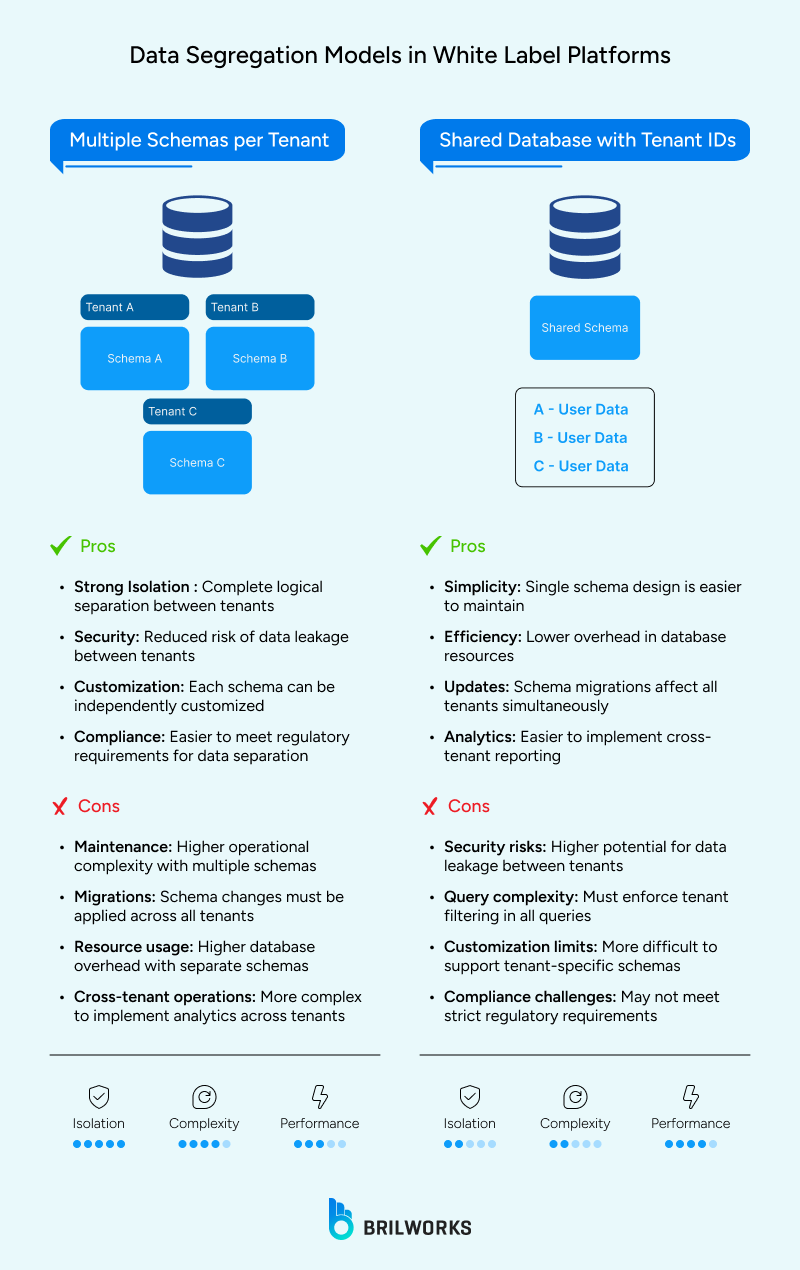
What you can do is isolate the tenants. You can achieve isolation within a shared environment. In one example, using a shared schema involves all tenant data existing in the same tables and separating the data using logic. This requires less work, has a smaller overhead footprint, and is easier to manage at scale, as long as every query filters on tenant ID.
Row-level security is another layer. You attach a tenant ID to every row and tell the database to enforce access rules. That means tenant isolation is maintained even if someone writes a poorly constructed query or does not validate tenant ID in the application.
Build and deploy robust custom solutions with our white label app development service, curated for startups and evolving businesses. Launch your SaaS application, while maintaining your brand identity across all digital touchpoints.
Another way to handle this is by setting up access control for each tenant. First, make sure you can tell which tenant is making the request. Once that's sorted, you can define what each user under that tenant is allowed to do, either by roles or by some kind of permission tree. Put a check in the middleware so nothing slips through.
If a user isn't allowed to do something, stop the request there. Keep it simple and predictable.
|
Layer |
Responsibility |
|
Auth layer |
Identify tenant + user |
|
Middleware |
Check tenant identity + permissions |
|
Business logic |
Verify user actions against roles/permissions |
|
Database |
Filter all data by tenant ID |
|
UI layer |
Show/hide actions based on user permissions |
In addition to this, automating testing can make this process relatively easier.
Types of automated tests to verify tenant boundaries
IAM and access control methods help organize who can do what. For multi-tenant apps, there are a few methods you can use to build a secure architecture.
Users Table
Contains users with a tenant_id column.
Roles Table
Stores roles like Admin, Manager, Viewer, with a tenant_id to make them tenant-specific.
Permissions Table
Stores actions like create_project, delete_invoice, etc.
RolePermissions Table
Links roles to permissions.
UserRoles Table
Links users to one or more roles.
When you're building a product that multiple companies use under their own branding (white-label), and each wants users to log in through their own identity provider (Google, Okta, Microsoft, etc.), SSO has to work per-tenant, securely, and without mixing things up.
Popular SSO protocols
|
Protocol |
Where It's Used |
Keep In Mind |
|
SAML 2.0 |
Used by older, enterprise systems |
Long-winded XML, but battle-tested. Validate signatures. |
|
OIDC (OpenID Connect) |
Modern option (built on OAuth2) |
Works well with Google, Microsoft. Watch for token validation. |
|
OAuth 2.0 |
For authorization, not login (use with OIDC) |
Don’t confuse it with authentication. |
Two-factor auth adds a second layer of security, beyond username and password. For a white-label SaaS, you need it to be secure, flexible for each tenant, and visually consistent with each brand.
These are the most common, supported, and reliable options:
Pros:
Cons:
Pros:
Cons:
Pros:
Cons:
Pros:
Cons:
Encryption is the tool that scrambles data so only the right people can read it. When working on white label projects, protect data by encrypting it wherever it lives, on disks and while moving between systems. Don't use default settings; pick proven encryption methods. Keep your keys separate from the data, and change them regularly.
Only keep data you actually need; don't store extras "just in case." Limit access tightly; only those who need it should get it. Encryption helps, but it's not enough on its own. Combine it with strict controls and regular checks.
When building white label platforms, you need to keep tenants clearly separate and control who can do what. Track what happens for each tenant so you can check compliance without confusion. Use tools that can tell which data belongs to which tenant and keep an eye on unusual activity.
You'll want to watch for things like failed logins, data being changed without permission, or unexpected access. Tools like Splunk or Datadog can help by letting you filter events by tenant.
Audits are important because they show if your rules actually work and if anyone's breaking them.
For logging, keep records that can't be changed, include tenant details, and keep them as long as the rules say.
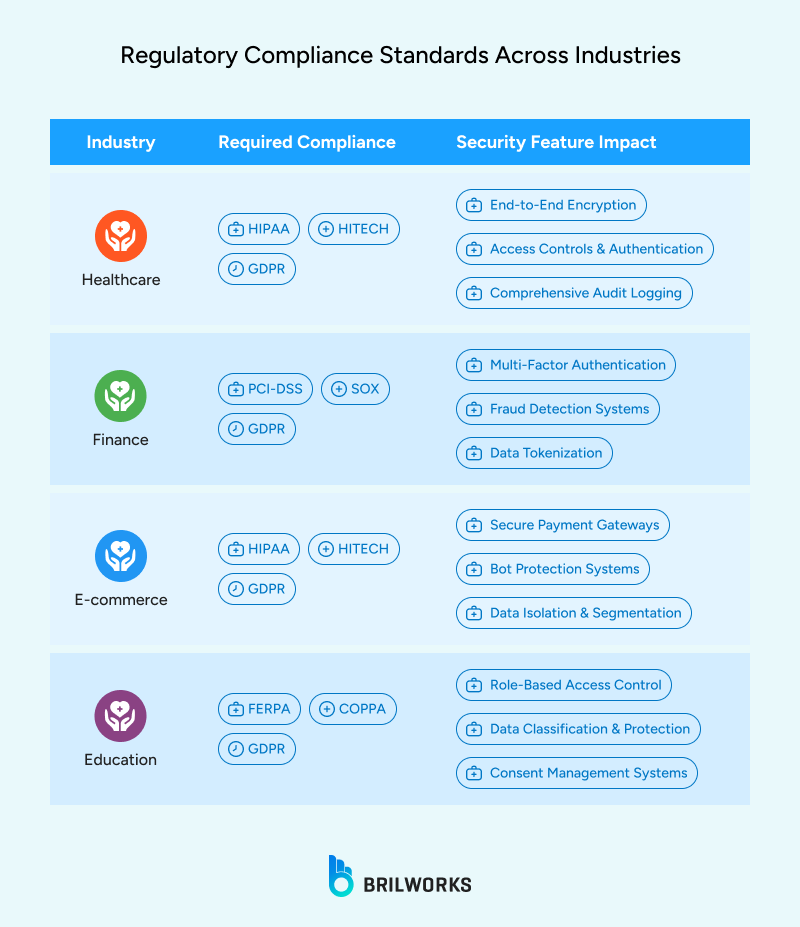
Regulations like GDPR, HIPAA, and PCI-DSS set rules on handling personal, health, and payment data. Each requires you to be careful about how you store and share data in a shared system.
Customization is a crucial feature of a white label product; clients expect their branding, colors, and style to be prominently featured. But these custom touches can't come at the cost of security. Customization should adhere to clear boundaries to prevent it from opening doors for attacks or data leaks.
One way to keep it safe is by handling client assets like logos and design files carefully. Store and serve them securely to prevent tampering. When clients add custom styles or CSS, sandbox those changes so they don't affect other parts of the system or other tenants. Always validate any branding inputs; don't trust what's coming in without checks.
To safely support extensions or plugins that clients want to add, set up a security review before anything goes live. Keep third-party code isolated to prevent it from interfering with core systems or accessing data it shouldn't. Define strict permission limits to ensure extensions only perform what they're allowed to do.
When clients upload assets, such as images or scripts, validating those files is crucial. Review their format and content, and implement content security policies to block malicious code. Run scans or verification routines to catch anything suspicious before it's accepted.
This approach keeps the platform flexible enough for customization while remaining secure enough to stay locked down.
Growing a white label system while maintaining security requires careful planning. As more clients join, the system must keep their data separate and run smoothly.
Adding servers helps handle more users, but security can't be left behind.
Keeping the system up during problems means thinking through security carefully.
Performance matters, but not at the cost of security. Here's how to keep things fast without risks:
This way, the platform stays both quick and safe as it grows.
We've explored how a security-first approach in white label development supports long-term growth. These measures don't slow you down; they make client onboarding faster and customization safer.
A strong security base gives your platform the freedom to scale without compromise. As a white label development company, Brilworks combines consulting and product engineering services to help businesses build secure, reliable solutions. Get in touch with us for a free consultation to discuss your white label security needs.
Implement a comprehensive security testing program that includes penetration testing, tenant isolation testing, and third-party security audits before your white label solution goes live.
Use a secure DNS configuration with proper SSL/TLS certificate management that isolates each tenant's domain while maintaining your infrastructure's security boundaries.
Implement tenant-aware authentication, rate limiting, and access controls for all APIs, ensuring each client can only access their own data while maintaining consistent security across all integration points.
Pursue industry-relevant certifications like SOC 2, ISO 27001, or HIPAA compliance depending on your target market, as these demonstrate your commitment to maintaining robust security controls in your multi-tenant environment.
Get In Touch
Contact us for your software development requirements
Get In Touch
Contact us for your software development requirements